What’s my path again? Why did my command fail?
Ever get ‘command not found’ errors when calling a command on a machine? Many times, these errors are related to what is defined on said machine. So with monitoring tools like SCOM, ALA, Azure Automation, BMC Patrol, the ID used in monitoring rely on filepaths defined on the local server (holds true for Windows/UNIX). Because sometimes even ls, awk, dir, etc. if their various bin directory filepaths are NOT specified as a security hardening measure. The result of STIG/Security hardening is ALL scripts/commands require a fully qualified filepath.
Fully qualifying command paths holds true for Windows and UNIX, from generic OS commands, AND also application specific files (including an executable). Updates are required if you want to supply the short name command. Add the full filepath to PATH= statement. The alternative is to fully qualify in your SCOM mgmt. pack, so the command will run regardless of user, as long as the path is correct.
Check for specified shell
First, let’s check UNIX to see what shell is specified for user(s).
Second, log into your UNIX server, and check files type: ls -al .* | more
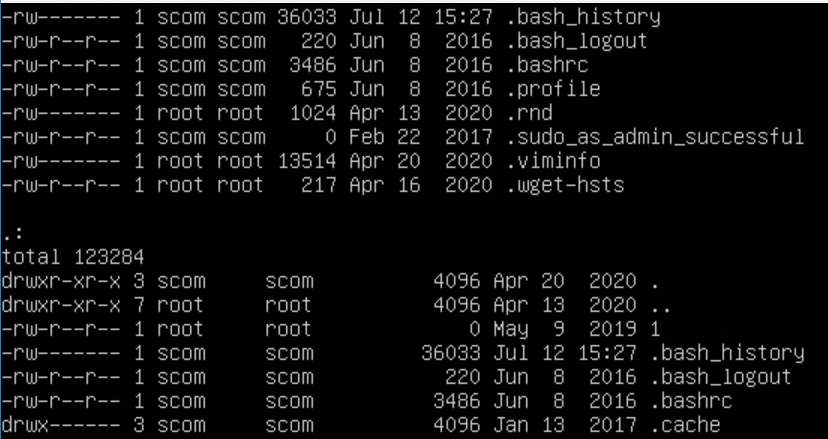
Third, another option with less output
example: ls -al .*profile

Fourth, Look for the shell defined for the user account
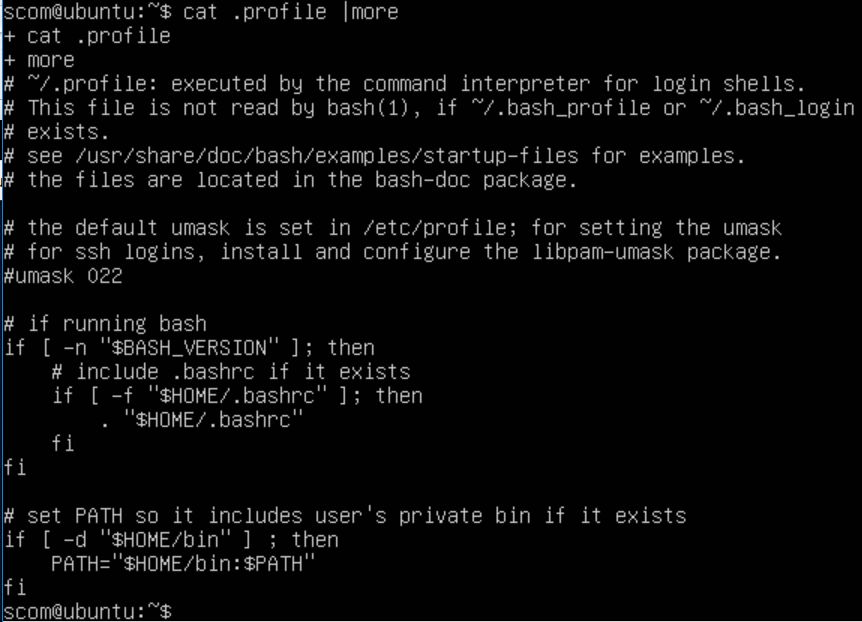
On my server, SCOM user is bash shell (but I do NOT have a .bash_profile, only a .profile (also note NO .ksh_profile) ) Knowing what profiles are configured for user account will help define what is inherited from the OS, (automatically included). Leverage when calling commands in your management packs for custom rules/monitors.
In conclusion, if executable is NOT in the filepath variable, you have two ways to resolve the issue:
- Create a .bash_profile
- Call bash/ksh shell in your script or command line: bash; <commandhere>
To check path:
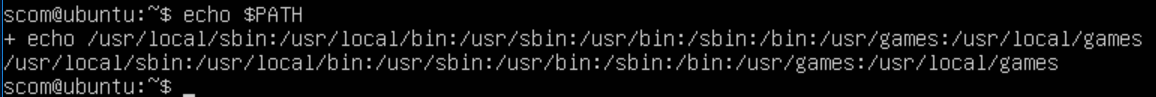
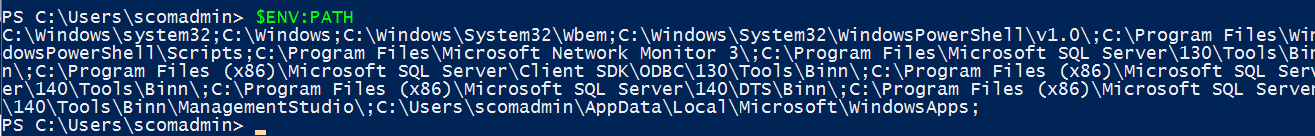
UNIX $PATH vs. Windows $ENV:path
UNIX example – ‘echo $PATH’ from UNIX ssh session/logon
Windows PowerShell example
Here’s my .profile that sets up SCOM user (only /bin shown)
Here’s a UNIX .profile example:
https://www.unix.com/unix-for-dummies-questions-and-answers/21995-basic-profile-setup.html
Example
set PATH=$PATH:/usr/homes/myhome/sqlldr:/appl/oracle/product/9.2.0/bin