
What are you Fluent in?
Don’t worry, if you’re on the edge, this may be a Scotty moment of “I’m giving her all she’s got” with your current monitoring environment.
Maybe you’re thinking ‘convince me’, so what does FluentD provide monitoring wise?
- System Center Operations Manager (SCOM) 2016+ has enhanced log file monitoring capabilities for Linux servers.
- Wild card characters in log file name and path.
- New match patterns for customizable log search
- Use community published plugins versus having to build from scratch
I wanted to take a moment to validate the steps provided, not just because I’ve had a pretty large part of my career supporting cross-platform environments for large enterprise companies. So, let’s get started!
Review the FluentD setup procedure
Let’s speed up the ‘do’ part. Review the procedure at docs.microsoft.com
FluentD basic operation here
Configuration Overview here
FluentD pre-reqs
Server types are covered = Linux (RedHat/Ubuntu)
Management Packs required for SCOM
- Load latest Linux Operating system management packs (2019).
- Find the pack download here
- Load the relevant Linux or Universal Linux packs
- Verify Microsoft.Linux.Log.Monitoring pack is loaded
Verify ID/password and sudoers capability for root
Use docs article if you need additional assistance to install agent on the Linux server. Alternatively, use my blog posts for PowerShell or GUI install
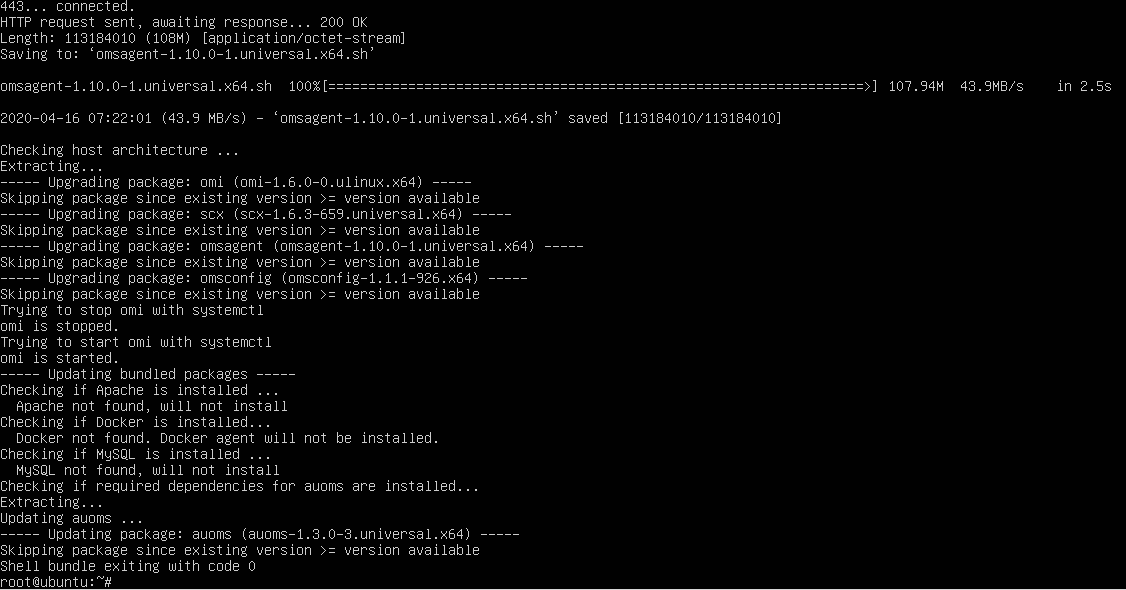
Update agent to latest release
Grab the latest OMS Agent release from github
- From server command line:
wget https://raw.githubusercontent.com/Microsoft/OMS-Agent-for-Linux/master/installer/scripts/onboard\_agent.sh
sh onboard_agent.sh
- The wget command above will install the OMSAgent and it’s pre-req packages
- This includes OMI, scx, OMSAgent, OMSConfig, auoms, Apache, Docker, MySQL (if the last three apply to your Linux server)
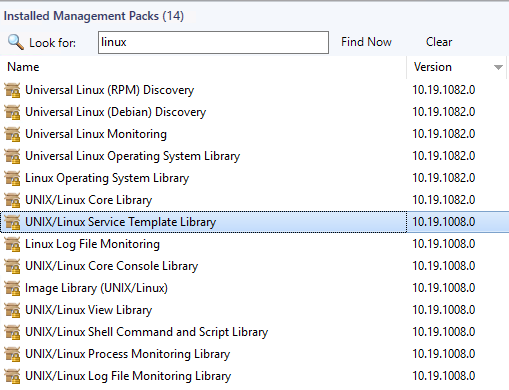
Load Management packs from latest UNIX release.
Verify packs are version 10.19.1082.0
Navigation steps:
From SCOM Console > Administration Tab > Installed Management packs
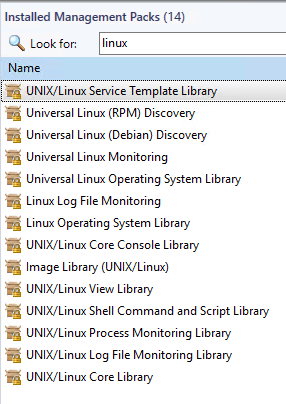
After adding the updated Linux Management packs
Linux server screenshots installing OMSAgent via wget command


Stay tuned, I’m currently testing FluentD configuration on my 2019 UR1 lab environment on Ubuntu16.


































