‘NiCE VMware addendum’ enhances VMware monitoring, tuning alerts to ‘manual intervention’ required alerting. The NiCE folks have been around for some time as a trusted Microsoft partner, creating additional monitoring functionality across Microsoft products. Having completed a number of projects implementing the VMware pack, it’s time to share the configuration and alert report capabilities.
Quick Download HTTPS://GITHUB.COM/THEKEVINJUSTIN/NICEVMWAREADDENDUM/
Changes to Nice vmware pack
Key breakdown of VMware ESX environment monitoring

Adjustments to vendor pack to further the mantra ‘alert when manual intervention required’.
Set monitor alerts to multiple samples over an hour (i.e. compute and performance of ESX environment)
Reports by team (requires regular expression updates for environment servers owned by each team)
Monitor reset logic, and service monitorType (count logic for X failures over Y time, before alert)
Overrides to change vendor pack provided discoveries, rules, monitors
Remove alert noise for unmanaged objects in ESX environment
Customize pack for environment
Customize the ‘NiCE VMware addendum’ pack for specific environment. This means updating group discoveries, and GUIDs for group specific overrides. Further updates are required to update server naming conventions for team virtualization reports.
Classes/groups created for pack
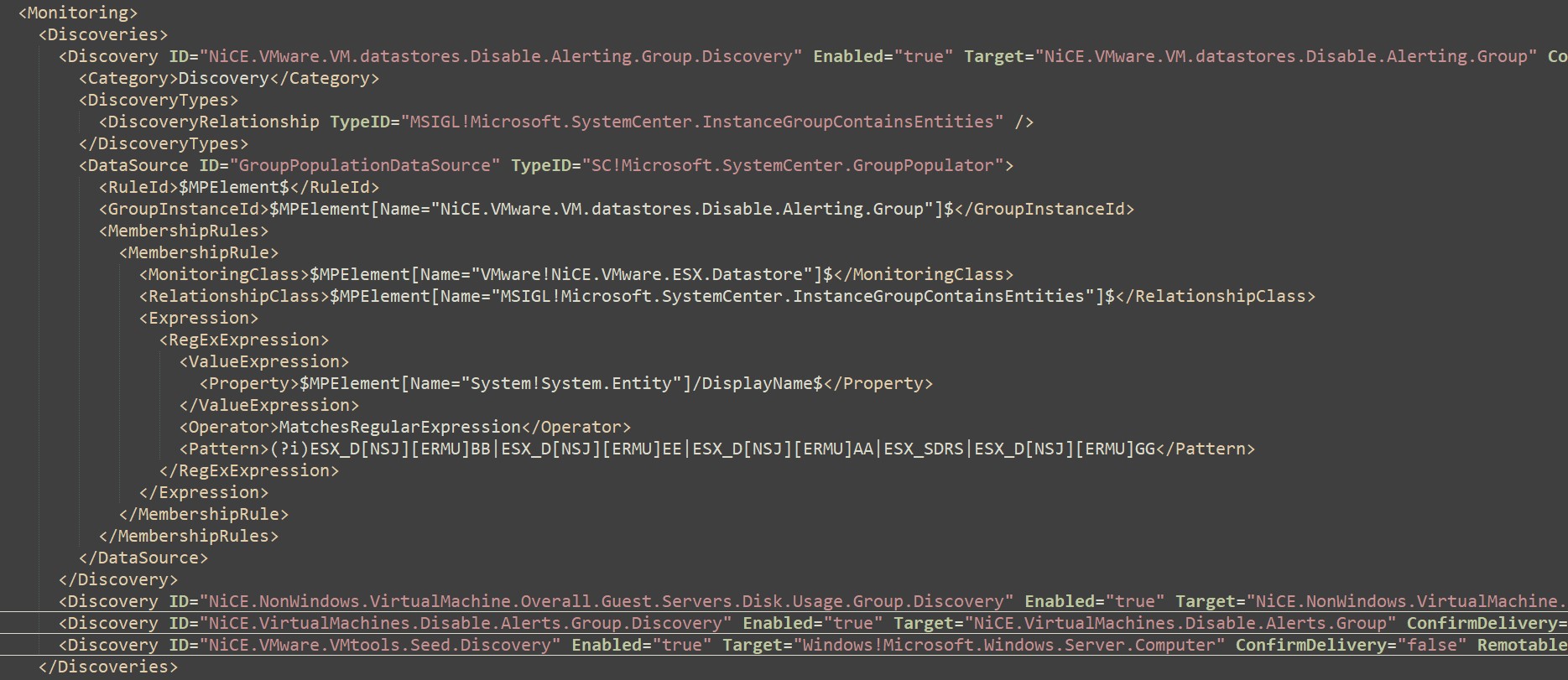
Discoveries
Breakout of Discoveries that need pattern updates to match
Find/Replace ##ESXHostDataStoreNamingConventions## with names to exclude
Example of regular expressions for multiple customers
Update disable guest machine alerts
Disable guest machines in ESX environment to disable alerts.
Find ##ESXGuestServersDiskUsageNamingConventions##
Replace with relevant guest naming conventions
Example template/guest/virtual machine names typically disabled
Service MonitorType
Service MonitorType adds Samples and Intervals to alert after consecutive failures (x failures in y minutes then alert )
Rules, Monitors, Recoveries
List of workflows used to troubleshoot/resolve problems
Documentation
NiCE VMware management pack https://www.nice.de/nice-vmware-mp/